This is really good for encrypted content such as a hard drive, password vault or gpg key
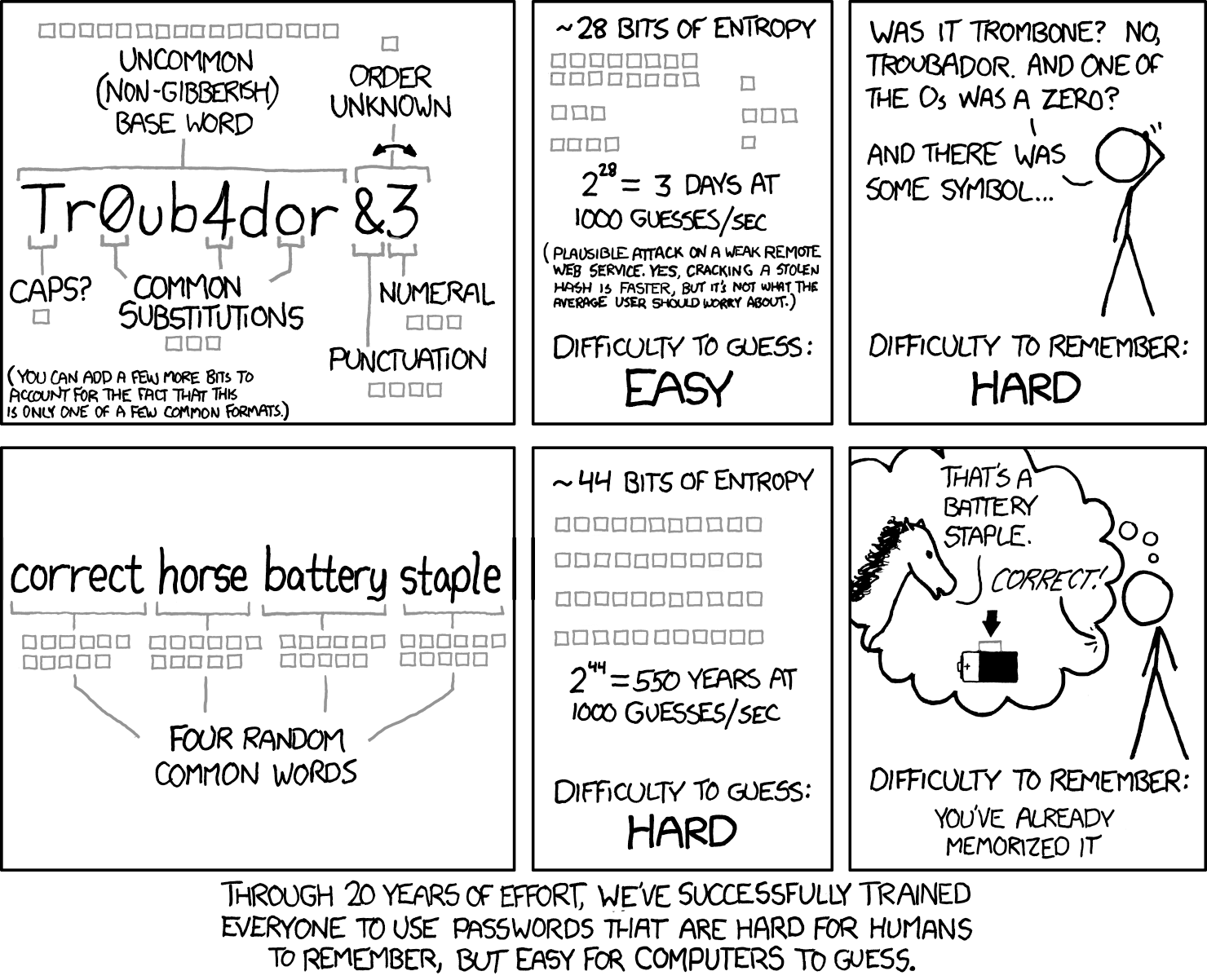
So TL;DR, the XKCD method, but with six words instead of four and using a larger wordlist?
Neat, and if you want a physical item to prompt you to do so https://www.crowdsupply.com/dicekeys/dicekeys can be an interesting option.
Nobody remembers diceware?
If you haven’t got any dice handy you can use random.org to generate the numbers for you. Or even select a set of words from the list
select a set of words from the list
I would be very careful doing this. It is very easy to introduce significant bias. Humans are terrible at picking random numbers.
If you can’t find dice I would recommend:
- Having a computer pick random items for you.
- Renumber the list into binary and flip a coin 12 times for each word. (This results in a slightly shorter word list but should be string enough).
#!/bin/bash head -$[$SRANDOM % `wc -l /usr/share/dict/words | cut -f1 -d' '`] /usr/share/dict/words | tail -1Doesn’t using a particular wordlist limits choice, gives attackers a wordlist to generate the password from
Nope, As long as you’re not as uncreative as to use Correct Horse Battery Staple.
Well it still technically does give them a list, it’s just that even with the list there are a lot of combinations.
deleted by creator
Even a “traditional” password would have a “list” that attackers could know (all the possible characters that can be used in a password), now compare this set of ±150 characters with the set of possible words that can be used (probably close to 250k per language if you take out some similarities).
Even with only 4 words, the number of possibilities is astounding.
Technically, yes. But the article already mentioned the amount of effort for the brute force to succeed (that is, practically never, if the phrase is truly random.)
But anyway. With regular passwords, the attackers already have a list: the alphabet plus numbers and symbols. Not really that different.
It does limit choice, but so long as you aren’t retaining the generation list somewhere an attacker can find it, how are they to know your list? As long as your list is incorporating less common words, your attacker can’t even simplify the problem by focusing on the most common words. Just one rare word can expand the list they need to use by tens of thousands of words.
Yes, but when the list is long enough and you have enough words, it is to difficult to guess.
Think about it. The list of all possible characters is also known, still with enough length and randomness it becomes too difficult to guess too.
Just mispel a word, replace a vowel with a numb3r and the wordlist is useless






