Wow, this is a very complex exploit, involving bits of iMessage and an undocumented CPU feature that allowed the attacker to evade hardware memory protection. From what I can see, Lockdown mode would have prevented this. The attacker is ridiculously skilled regardless
Exerpts from the article missing from the bot summary:
The mass backdooring campaign, which according to Russian officials also infected the iPhones of thousands of people working inside diplomatic missions and embassies in Russia, according to Russian government officials, came to light in June. Over a span of at least four years, Kaspersky said, the infections were delivered in iMessage texts that installed malware through a complex exploit chain without requiring the receiver to take any action.
With that, the devices were infected with full-featured spyware that, among other things, transmitted microphone recordings, photos, geolocation, and other sensitive data to attacker-controlled servers. Although infections didn’t survive a reboot, the unknown attackers kept their campaign alive simply by sending devices a new malicious iMessage text shortly after devices were restarted.
The most intriguing new detail is the targeting of the […] hardware feature […]. A zero-day in the feature allowed the attackers to bypass advanced hardware-based memory protections designed to safeguard device system integrity even after an attacker gained the ability to tamper with memory of the underlying kernel.
someone was made fun of one too many times about having green bubbles in imessage
With that many exploits being used I wouldn’t be surprised to see it is a group probably government sponsored. They love iMessage exploits as original attack vectors too.
Documentary about the pheonix software explains a lot about who used this kind of virus, mainly political figures and govermants to spy on other politicans and jornalists. The imessage exploit was known for a few years but nobody knew how the file installed itself on the device, so there was no way to figure out how to protect the device.
Which documentary?
It’s not purely talent that allows them to make this kind of stuff. Otherwise people outside of these agencies would be making this stuff too. It’s also the fact the CIA or any of the others can go to apple for example and get all of the information on how these chips are made and the firmware on them, then put the company under a gag order.
It is silly to assume the governments hackers are any better then a good hacker that doesn’t work for them. And you need to realise that their advantages come from legal power, resources, and lesser regulations on research.
Because a lot of silly conspiracy theories seem to stem from people believing that the government are somehow superior beings, when the only thing that makes them different from anyone else is power.
Yup. The government has historically had issues keeping good hackers on their payroll. Because the good ones can make way more money in the private sector, so what incentive do they have to actually stick around?
There’s also the issue that the federal government has been required to drug test due to regulations requiring all federal employees to be tested. And good luck finding a good hacker who would be willing to take a drug test.
The only real edge the government hackers have is that they can force companies to give them insider access.
If you hire the hackers that tried to hack you instead of sending them to prison, you can fix the talent retention problem, but I think they already figured that out. Wonder if the kid who hacked GTA is being looked at in that way or if they don’t want to deal with his mannerisms.
Dude hacked again from within his hotel using the tv right? I wonder who’s in charge of doing that math. Hacker skill vs idiosyncrasies
This happens rarely, and if it happens, the chances of it being someone we know from the media are almost 0; that would be all under the table. The “best” are the ones you don’t hear about because they are too busy working on actual stuff, same in most science fields.
Most of them are recruited in “normal” ways; there is much more talent around these days. No need to engage with criminals and put them on actual sensitive stuff. Also, they get paid more than you might think; the people leading these projects are not stupid and make a simple mistake like underpaying talent they still need.
wasn’t that a social hack mainly? what need would they have for social engineering.
They consider him insane. They aren’t letting him close to anything important.
The exploit’s sophistication and the feature’s obscurity suggest the attackers had advanced technical capabilities
exploiting a vulnerability in an undocumented hardware feature that few if anyone outside of Apple and chip suppliers such as ARM Holdings knew of.
according to Russian officials also infected the iPhones of thousands of people working inside diplomatic missions and embassies in Russia
the devices were infected with full-featured spyware that, among other things, transmitted microphone recordings, photos, geolocation, and other sensitive data to attacker-controlled servers
Sounds like government espionage
puts tinfoil hat on
4 zero days means they bought it on black market at least.
This is the best summary I could come up with:
Researchers on Wednesday presented intriguing new findings surrounding an attack that over four years backdoored dozens if not thousands of iPhones, many of which belonged to employees of Moscow-based security firm Kaspersky.
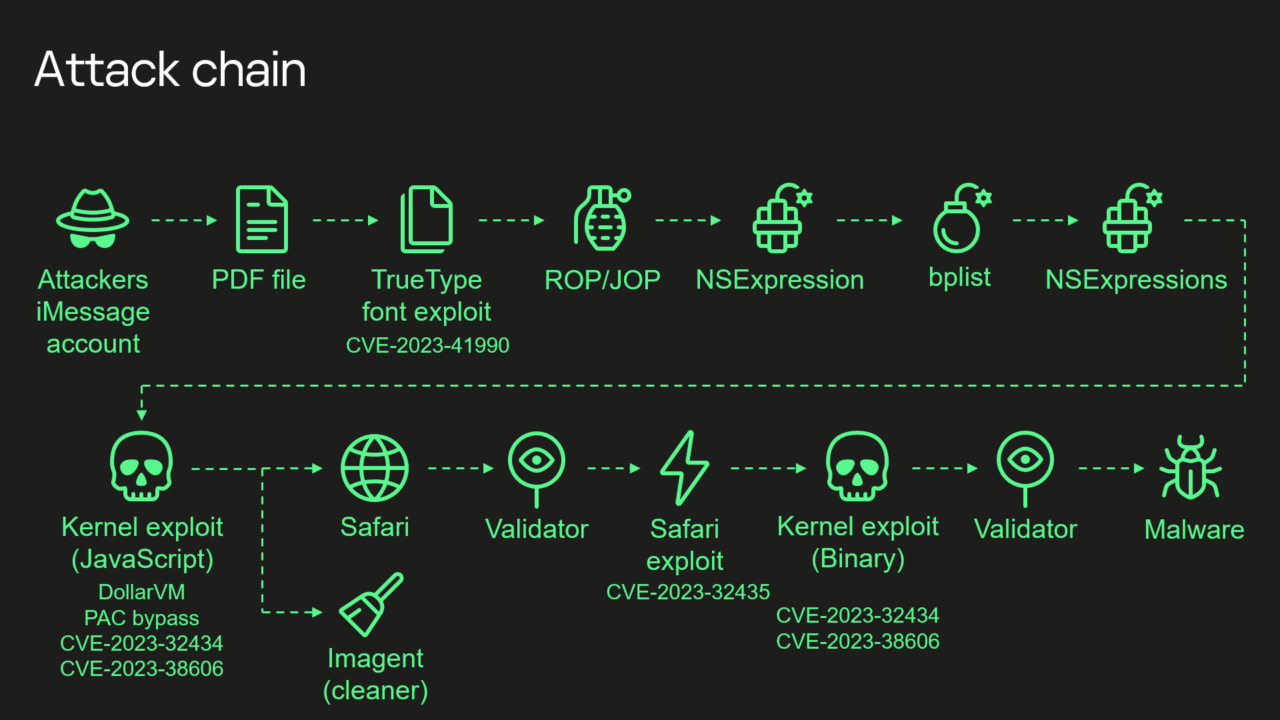
Chief among the discoveries: the unknown attackers were able to achieve an unprecedented level of access by exploiting a vulnerability in an undocumented hardware feature that few if anyone outside of Apple and chip suppliers such as ARM Holdings knew of.
“The exploit’s sophistication and the feature’s obscurity suggest the attackers had advanced technical capabilities,” Kaspersky researcher Boris Larin wrote in an email.
“Our analysis hasn’t revealed how they became aware of this feature, but we’re exploring all possibilities, including accidental disclosure in past firmware or source code releases.
A fresh infusion of details disclosed Wednesday said that “Triangulation”—the name Kaspersky gave to both the malware and the campaign that installed it—exploited four critical zero-day vulnerabilities, meaning serious programming flaws that were known to the attackers before they were known to Apple.
The researchers found that several of MMIO addresses the attackers used to bypass the memory protections weren’t identified in any device tree documentation, which acts as a reference for engineers creating hardware or software for iPhones.
The original article contains 653 words, the summary contains 200 words. Saved 69%. I’m a bot and I’m open source!
Can’t wait to listen to the Darknet Diaries interview about this in a few years.
How do you find those podcasts, sometimes the stories are really interesting but I think he is running thin on ideas.
not op, but I think it depends a lot on the person he’s interviewing
I wonder how many of those exploits were long known by the three-letter agencies, and were hoarded instead of getting fixed.
It’s important to reboot your devices frequently
Does ios have any ROP mitigations?
Can the US government pass a law to force Apple specifically to rip out the messages app and replace it with something that apparently doesn’t have infinite exploits??
There is no such thing as a device or software without exploit, even a carrier pigeon can be cought and the messege read.
What if the pigeon has a gun?
That’s it boys. We’ve found the answer. Pack it up
You are thinking of exploding penguins.
iGun patch incoming
Not if you wirte the message using invisible ink.
Not if you never write the message, more like
I wouldn’t trust a service whose source code is not accessible though.
We may not have carrier pigeon DNA readily available, but it is certainly accessible!
How would that help them? Even if that were an effective measure (which it isn’t), it was almost certainly a us spy agenciy that did this.
Not necessarily, five eyes share intelligence responsibilities